Donald Trump called for a sweeping ban on Muslims entering the United States soil and Anonymous declared war against him.
Report: breached records count down this year
The number of individual records compromised by data breaches has declined by 41 percent during the first half of this year, compared to the same period last year, even as the number of breaches went up, according to a new report by Gemalto.
Web.com hacked, at least 93,000 credit card data exposed
The US-based web hosting company Web.com has been Hacked, it admitted that credit card information of 93,000 customers have been compromised.
Web.com is the last victim of a data breach, the US-based web hosting company has up to 3.3 Million customers. According the first news circulating in the Internet the hackers may have compromised personal information and credit card data belonging to 93,000 of Web.com 's clients.
Web.com discovered the breach while conducting ordinary security monitoring and shutdown process, the company confirmed that unknown hackers breached one of its servers on August 13 and accessed customers' data.
"Web.com, (Nasdaq:WWWW) reported that it discovered an unauthorized breach of one of its computer systems on August 13, 2015. As the result of this attack, the credit card information of approximately 93,000 customers (of the company's over 3.3 million customers) may have been compromised. The company uncovered the unauthorized activity through its ongoing security monitoring. The company immediately reported the attack to credit card processors and the proper federal and state authorities." reports the official statement released by Web.com.
The stolen data includes:
Credit Card information
Actual Names associated with the payment cards
Residential Addresses
According to the company no other information belonging to its customers, such as Social Security numbers, Verification Codes for the exposed credit cards, was exposed by the cyber attack.
At the time I was writing there are no other details on the incident, for example, it is not clear how hackers compromised the company server and if the stolen data was encrypted.
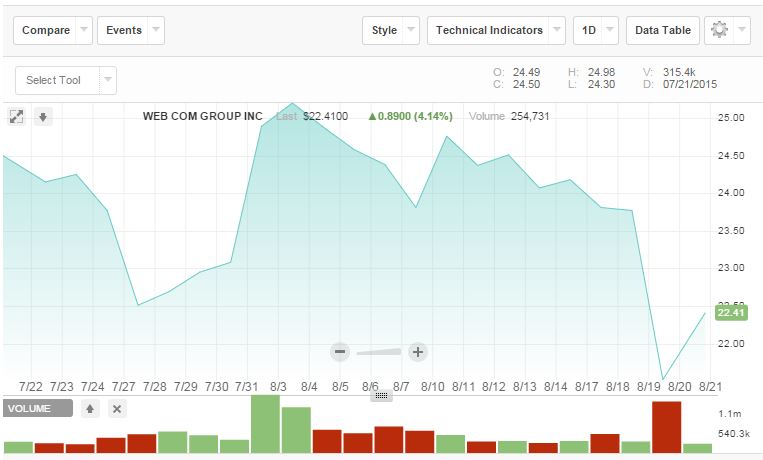
The impact of the data breach was serious with repercussion on the value of its shares after the disclosure of the incident.
Web.com reported the cyber crime to law enforcement which are currently investigating the data breach.
However, neither the company mentioned whether the stolen data was encrypted, nor it said how hackers were able to accessed its customers' data.
"The security of our customer information is a high priority for Web.com," Web.com CEO and Chairman David L. Brown stated in a statement. "Our goals are simple –to protect our clients from the Internet attacks and, in the event that an attack succeeds, to fix the [issue] immediately."
Web.com has already notified the incident to its customers via email, it will also provide Free Credit-Monitoring Protection for one-year to users affected by the intrusion.
Tor security concerns prompt largest dark market to suspend operations
Agora, the Tor network's largest black marketplace, has been temporarily shut down because its administrators worry the website is vulnerable to recent methods of exposing Tor Hidden Services.
The largest of these so-called dark markets was Silk Road, which was eventually shut down by the FBI in 2013. Many similar websites have appeared since then and some were targeted in subsequent international law enforcement raids, but Agora survived and surpassed even Silk Road in size and popularity.
In a message posted Tuesday on Agora and signed with a PGP key used for official communications, the website's administrators announced that they're taking the market offline. The stated reason was recent research about vulnerabilities in the Tor Hidden Services protocol that could be exploited to de-anonymize server locations.
The Agora administrators are working on a solution that will require "big changes" to the site's software stack, and it will take time to deploy, according to the message.
"Additionally, we have recently been discovering suspicious activity around our servers which led us to believe that some of the attacks described in the research could be going on and we decided to move servers once again, however, this is only a temporary solution," they wrote.
It's not clear which specific research the Agora administrators referred to, but a paper presented at the 24th USENIX Security Symposium two weeks ago seems to fit their description. The paper, authored by researchers from the Massachusetts Institute of Technology (MIT) and the Qatar Computing Research Institute (QCRI), describes a new traffic fingerprinting method that improves upon previous techniques and could allow attackers to determine with a high degree of accuracy where Hidden Services are hosted.
"Most of the new and previously known [de-anonymization] methods do require substantial resources to be executed, but the new research shows that the amount of resources could be much lower than expected, and in our case we do believe we have interested parties who possess such resources," the Agora administrators said.
Those interested parties are likely law enforcement agencies.
Judging by comments on Reddit, the decision to temporarily take the website offline until a solution is implemented, was largely appreciated by Agora users, especially since it's in line with the market's primary rule: "Anonymity is sacrosanct here."
The MIT and QCRI research paper proposes countermeasures that could be built into Tor itself. When reports about the research first appeared in July, the Tor Project said that it will analyze the proposed changes to the protocol to determine if they would indeed make hidden service fingerprinting harder.
Hackers show off long-distance Wi-Fi radio proxy at DEF CON
A talk about a radio-based privacy device dubbed ProxyHam that promised to allow hackers to connect to Wi-Fi networks from as far as 2.5 miles away was abruptly pulled from the DEF CON schedule by its creator a few weeks ago.
The incident, which some speculated was the result of pressure from the FBI or the NSA, outraged the security community. But as hackers are not the type to give up easily, they quickly came up with a replacement that in many respects is better than the original.
Called HamSammich, the new device is the creation of security researchers Robert Graham and David Maynor and can proxy data over the 900 Mhz radio band from 20 miles away at up to 56kbps -- the top speed of a dial-up modem from the late 1990s. It was presented at the DEF CON hacking conference on Friday.
The idea behind ProxyHam and HamSammich is that a user can install the device in a public place, connect it to a free Wi-Fi hotspot and then relay the connection over the 900 Mhz band to a computer that's equipped with a powerful antenna pointed at the location of the first device. This would make the user appear to be physically in one location while in fact he would be miles away.
The problem with the ProxyHam concept is that its creator, a researcher named Ben Caudill, believed that no one monitors the 900 Mhz band, but in fact it's quite easy to see the signal and track it, Graham and Maynor said.
The two researchers believe that the more likely explanation for the talk's sudden cancellation was that Caudill's activity was discovered by the Federal Communications Commission because he boosted the transmit power to levels that are not allowed. He was also using encrypted signals over the 900 Mhz amateur (ham) radio band, which is also against regulations.
The FCC has people watching the radio frequencies in all cities, so the agency probably tracked him down and made him sign a consent decree that prevents him from engaging in this type of activity in the future, Graham said.
HamSammich takes a different approach. It uses a very weak signal, but spreads it out using many software-defined radios. The signal is kept behind the noise floor, which puts in the range of radio interference caused by natural phenomenon like thunderstorms and man-made devices -- the background noise one hears when tuning a radio.
This severely limits the device's connection speed, but increases its range. And while the signal can still be tracked with specialized equipment, there's a good chance that no one is looking.
Nobody will complain if your added noise is below the background noise, Graham said. The transmitted data is not encrypted, but that's not of great concern if no one knows it's there, he said.
Caudill's company, Rhino Security Labs, which announced the talk's cancellation in July, did not immediately respond to a request for comment.
However, Caudill told Wired in an interview last month that the FCC had nothing to do with it. At the time, Rhino Security also said that it was immediately halting development of ProxyHam, that it wouldn't release any more details about the device and that existing units would be "disposed of."
Who are the Ashley Madison users?
The hackers behind that data breach of the Ashley Madison website have released another dump of 20 GB and experts are publishing their analysis on it.
The recent hack of the adultery website Ashley Madison is attracting the attention of the media, after the disclosure of a second dump of data the security experts started their analysis on the leaked information.
Today I decided to propose you an interesting point of view proposed by the marketwatch.com which published a post to highlight that hundreds of email addresses in the Ashley Madison data dump are in big banks' domains. MarketWatch analyzed data provided by the popular security researcher Robert Graham, CEO of the Errata Security firm.
This news is not surprising for me, but evidently someone still believes that there is a substantial difference between users of the adultery website. The report correctly noted the wrong security posture of hundreds of bankers which used their work email addresses to register for Ashley Madison website.
Analysts from MarketWatch analyzed the email addresses and found at least 665 emails associated with major financial institutions.
Bankers aren't the unique unwary users, according to the Hill the dump of the Ashley Madison data includes more than 15,000 government and military emails.
We have also to consider that the AshleyMadison.com doesn't verify users' email addresses in the sign in process, which means people can use fake emails or email accounts belonging to other individuals.
[Ashley Madison] "actively monitoring and investigating this situation to determine the validity of any information posted online and will continue to devote significant resources to this effort." states Ashley Madison in a statement published on the adultery website.
Below the list of financial institutions:
Wells Fargo — @wellsfargo.com: 175
Bank of America — @bankofamerica.com: 76
Deutsche Bank — @db.com: 73
Citigroup — @citi.com: 51
Goldman Sachs — @gs.com: 45
PNC Bank — @pnc.com: 28
U.S. Bancorp — @usbank.com: 15
Bank of New York Mellon — @bnymellon.com: 14
J.P. Morgan Chase — @jpmchase.com: 9
Capital One — @capitalone.com: 4
"While we cannot speak to the veracity of the data, as a matter of company policy we require that team members use personal email addresses to conduct personal business," Wells Fargo spokesman Ancel Martinez told MarketWatch.
At this point, there are two things to seriously consider, bankers are a privileged target of cyber criminals that could use this data to run further attacks in an attempt to steal sensitive data. Another disconcerting consideration to do is related to the use of corporate asset made by bankers and more in general by employees that could expose the company to risk of hack due to lack of awareness of principal cyber threats.
Let me close with another interesting data related to the Ashley Madison hack, a researcher has mapped all the users to a Google Maps view showing that the majority of them are from Europe and US.
Ashley Madison users Maps
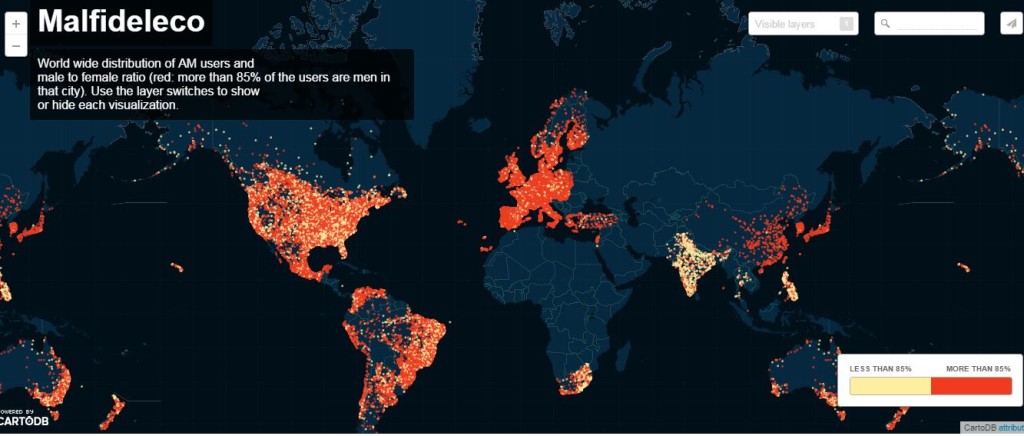
The research also claims that 85% of the Ashley Madison users are males.
This App Lets Anyone 3-D Print ‘Do-Not-Duplicate’ Keys
IN AN ERA when digital tools allow anyone to make practically anything, inscribing the words “do not duplicate” on a key only invites ambitious lock pickers to do exactly that. Now one group of researchers has released a piece of software that makes copying purportedly uncopyable keys easier than ever.
On Tuesday, a group of University of Michigan researchers released a new web based tool that lets users 3-D print any of thousands of “restricted” keys designed to defy copying attempts. Aside from the “do not duplicate” warnings on restricted keys, lock makers also try to prevent their duplication by using contorted keyways—the space inside a lock that a key’s inserted into—and selling the blanks that fit them only to users who can prove their affiliation with a big client like a corporation, university, or government agency.
But the researchers’ tool, which they’ve called Keysforge, is meant to demonstrate that those obscure key shapes no longer offer the security they did before accessible 3-D printing. With little more than the restricted key and a photo of the front of the lock, Keysforge can produce a CAD file ready to 3-D print a working key on any consumer-grade 3-D printer. “We’ve proven that restricted keyways are no longer a defense,” says Michigan researcher Ben Burgess. “We’ve shown that anyone with a 3-D printer can quickly and easily attack these systems.”
physical security measures, the Michigan researchers’ technique works on a wide array of lock systems that use the common A-2 standard of pin spacing inside a lock. Input the series of depth cuts that represent the key’s vertical contours—they can be found with a pair of calipers and achart like this one—and a front-facing photo of the lock it fits into, and the software can automatically generate a CAD file for a duplicate key. And unlike the Photobump creators, the Michigan researchers have also released their software to the public in a bid to definitively demonstrate that restricted keys can be easily copied.
Replicating restricted keys allows for more than the unlimited copying of a key by, say, a rogue employee: It could also make it possible to duplicate a high-security key from a photograph taken from a distance with a high-powered lens. Researchers showed in 2009 they could find the measurements of a key’s cuts from a photograph taken from as far as 200 feet away and at an angle. Like the earlier, unreleased Photobump software, the publicly accessible Keysforge software could enable the easy creation of bump keys for restricted key profiles. Or it could even allow what the researchers call “privilege escalation” attacks, like what University of Pennsylvania computer scientist Matt Blaze has demonstrated. Blazed showed that in a building or facility that uses master keys, a key holder can create a series of keys with small variations on his or her regular key and eventually create a master key that opens many more doors. Using Keysforge to build a series of 3-D printed keys would make that trial-and-error process vastly easier. “One of the biggest defenses for these methods was restricted keyways,” says Burgess. “This reopens those attacks.”
In addition to their proof-of-concept software, the researchers also tried to assess which 3-D printable materials work best for duplicating keys. They tested a variety of printable plastics, and found that the cheap polylactic acid (PLA) plastic used by the popular Makerbot line of 3-D printers was actually stronger than more expensive printers’ materials like acrylic and nylon. They found that stainless steel, which can be printed with mail-order services like Shapeways and iMaterialise, was strongest of all, but due to its hardness can damage the internals of a lock. The researchers instead recommend softer brass, which is also available from those commercial printing services. They plan to present all of their research at the Usenix Workshop on Offensive Technologies next week.
A Medeco spokesperson Clyde Roberson called the Michigan researchers’ work “important and informative.” He added that the company has been working to create locks with electronic and mechanical components that can’t be 3-D printed. “Medeco and [its parent company] ASSA ABLOY have been researching this topic and have been actively pursuing improvements in our technology to help minimize this threat,” Roberson wrote in an email. “This includes testing various scanning and printing devices available on the market, from highest quality to lowest. We have already developed some products directly as a result of this work and future products will continue to reflect added protection for this threat.”1
It’s safe to guess that the lock industry as a whole doesn’t appreciate 3-D printing tools like Keysforge, which chip away at its monopoly on restricted key blanks. But the Michigan researchers argue that their software is necessary to demonstrate—both to lock makers and to consumers—that merely restricting access to keys is no longer enough. Instead, they say, the industry needs to move toward high-security locks that integrate electronic security measures, or keys that have moving or magnetic components. “Attackers and criminals, especially the high end ones, will learn these attacks,” says Michigan researcher Eric Wustrow. “If this is a world where only the manufactures and the attackers know what’s going on, it’s dishonest to sell these [restricted keys] to consumers.”
“This lets consumers know what they’re buying—that restricted keyways won’t necessarily give them the best defense,” Wustrow adds. “And it shows lock manufacturers that they need to improve their designs.”