Exploits use Apple's enterprise app distribution model and 'private APIs' to seed adware on iPhones, sidestepping App Store inspections
Find a zero-day exploit to hack IOS 9 and win a $1m prize
Zerodium is an Exploit trader and it's offering a million dollar prize to any person that finds unknown, unpatched bug in iOS 9 with the main purpose to jailbreak iThings.
LG phones most exposed to new Certifi-gate vulnerability
More than 70 percent of Android phones from LG have a plugin installed that exposes them to the Certifi-gate remote support app vulnerability, where a rogue application -- or even a text message -- can completely take over a device.
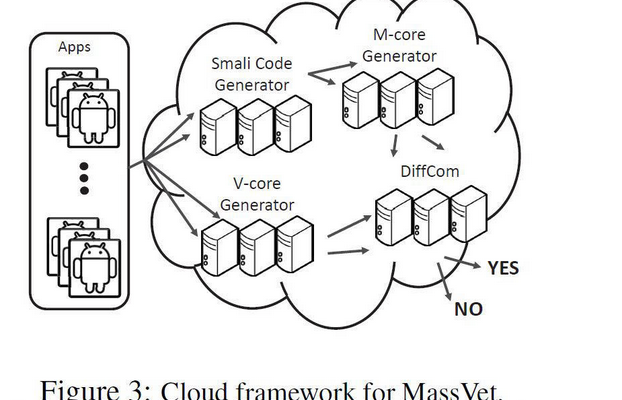
MassVet finds unknown malicious apps in app stores in 10 Sec
A group of University researchers has created a new method for detecting malicious apps running on an Android devices called MassVet. MassVet doesn't use the old method of signatures scanning, instead it compares legitimate Android frameworks to establish those that are malicious.
Apple users are vulnerable to sandbox vulnerability
Experts discovered that the sandbox vulnerability affects all apps that use the managed app configuration setting in devices that run older versions.
Researchers discover new keychain vulnerability in OSX
Antoine Vincent Jebara and Raja Rahbani, the co-founder and lead engineer of MyKi – an identity management company in Beirut - have discovered a vulnerability in Apple's password management system (Keychain), which if exploited, enables an attacker to compromise stored credentials at will.
Google Patches Vulnerability in "Google Admin" App for Android
Researchers identified a vulnerability in the Google Admin application for Android that could have been exploited to read arbitrary files from the app's sandbox. Google says it has released an update to patch the flaw.