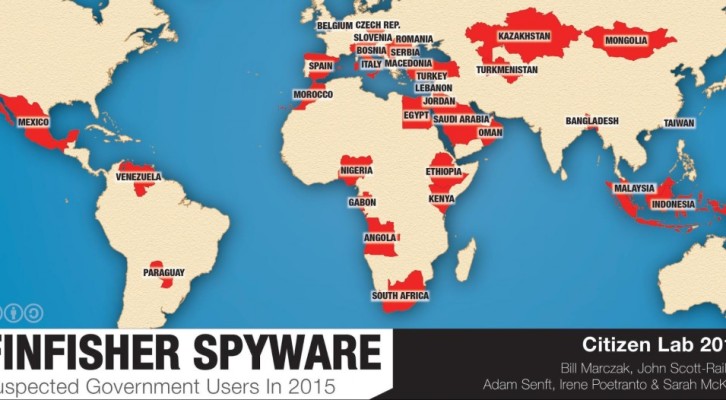
A new research conducted by Citizen Lab revealed that the number of governments using the FinFisher surveillance software has increased.
US state police cars are vulnerable to cyberattack
Virginia State Police (VSP) launched a project to test the resilience to cyber attacks of police cars (models 2012 Chevrolet Impalas and 2013 Ford Tauruses)
Another computer system at the Pentagon has been hacked
Another cyber attack hit computer systems at the Pentagon, this time the food court computers have been hacked exposing employees' bank information.
Identity theft hit 7% of US population last year
Almost 18 million people were victims of identity theft in the United States last year, with the majority of crimes targeting credit cards and bank accounts, the Department of Justice said Sunday.
North Korea exploits a 0-day in the South Korea’s principal Word processor
FireEye suspects that the North Korea is responsible for a number of attacks against the South Korea relying a 0day in the South most popular Word processor.
Russian military attacked, possibly by Chinese cyber group
Members of the Russian military have been receiving well-crafted phishing emails since mid-summer from attackers that use Chinese-language tools and Chinese command-and-control installations, according to a report released yesterday.
Leaked NSA Documents Show AT&T Helped Spy Agency: Report
The US National Security Agency has used a unique, decades-old partnership with AT&T to snoop on Internet usage, according to newly disclosed documents leaked by Edward Snowden.