A study released by a forensic consultancy has singled out the top five vehicles most susceptible to hacking.
The results of the study, by PT&C|LWG Forensic Consulting Services, were based on published research by hackers, vehicle recall information and media reports.
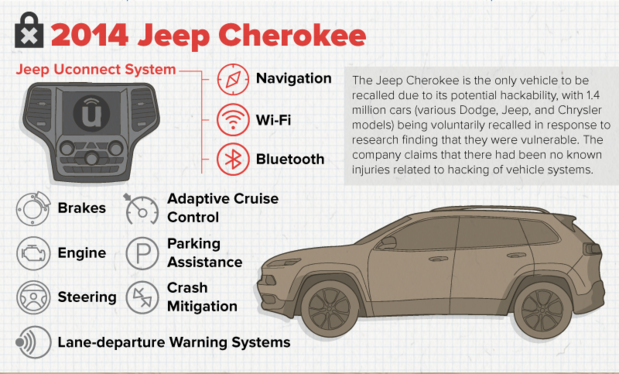
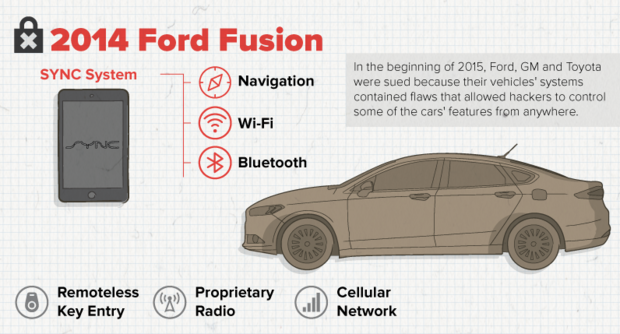
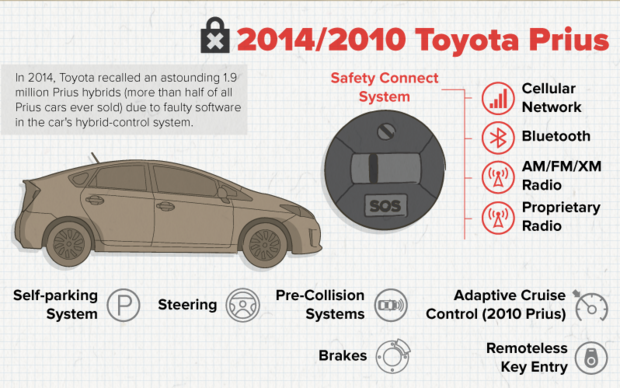
The most hackable list includes the 2014 Jeep Cherokee, the 2014 Infiniti Q50, the 2015 Cadillac Escalade, the 2010 and 2014 Toyota Prius and the 2014 Ford Fusion.
The study also includes the least hackable cars: The 2014 Audi A8, the 2014 Dodge Viper, the 2014 Honda Accord and the Tesla Model S (no particular year provided).
PT&C|LWG's least hackable car list was based on the vehicles having either fewer computer systems, such as the Dodge Viper, or fewer networked components communicating with each other, such as the Audi A8.
"So there just aren't as many access points," said Robert Gragg, a forensic analyst with PT&C|LWG.
Tesla was chosen as least hackable because the all-electric vehicle's head units are based on Linux.
"If you look at all the malware out there, it's written mainly for Windows OS systems. Linux is a more robust operating system and more difficult to write malicious code to," Gragg said.
Conversely, the cars with the highest risk of cyber threat tended to have the most features networked together, especially where radio or Wi-Fi networks are connected to physical components of vehicles, according to Gragg.
Gartner predicts that by 2020, the number of wirelessly connected passenger vehicles on the road will reach 150 million, and 60% to 75% of them will be capable of consuming, creating and sharing Web-based data.
To address the future threats posed by wireless hacking of vehicles, Intel today announced it has established the Automotive Security Review Board (ASRB) to help mitigate cybersecurity risks associated with connected automobiles.
The board will be comprised of top security industry talent across the globe, with particular areas of expertise in cyber-physical systems. The ASRB researchers will perform ongoing security tests and audits intended to codify best practices and design recommendations for advanced cybersecurity solutions and products to benefit the automobile industry and drivers. Intel also published the first version of its automotive cybersecurity best practices white paper, which the company will continue to update based on ASRB findings.
"We can, and must, raise the bar against cyberattacks in automobiles," Chris Young, senior vice president and general manager of Intel Security, said in a statement. "Few things are more personal than our safety while on the road, making the ASRB the right idea at the right time."
Today's modern automobile uses between 20 and 70 computers, each with its own specialized use. For example, engine control units oversee a wide array of electronic sensors and actuators that regulate the engine and maintain optimal performance. Vehicle manufacturers use the generic term "electronic control units" (ECUs) to describe the myriad of computers that manage various vehicle functions.
For example, ECUs control vehicle safety functions, such as antilock brakes and proximity alerts. And climate control systems are governed by an ECU that receives temperature data from sensors inside the cabin and use that to adjust air flow, heating and cooling.
Typically, all of a vehicle's computer systems can be accessed over a vehicle's controller area network (CAN) via the radio head unit, a computerized system that runs a car's or truck's communications and entertainment system.
Many of today's modern vehicles can be accessed via cellular, Bluetooth or even WiFi connectivity. While no easy task, once a hacker gains access to the vehicle's head unit, its firmware can be used to compromise the vehicle's CAN, which speaks to all of the ECUs. Then it's just a matter of discovering which CAN messages can control various vehicle functions.
For example, a security researcher recently posted a video on YouTube demonstrating how a device he made could intercept wireless communications to locate, unlock and remotely start GM vehicles that use the OnStar RemoteLink mobile app.
Another recent hack demonstrated how a 2015 Jeep Cherokee's CAN could be accessed via a cellular connection and everything from steering and braking to seatbelts and the radio could be remotely controlled.
The Jeep Cherokee hackers, security experts Charlie Miller and Chris Valasek, said because of cellular access, hundreds of thousands of vehicles are potentially at risk of being hacked from great distances.
The PT&C|LWG study estimated minimum distances from which a vehicle could be hacked according to the wireless communication protocol it is using.
For example, a passive anti-theft system could be access from 10 meters (33 feet), a radio data system (or radio head unit) could be hacked from 100 meters, a Bluetooth system could be accessed from 10 meters, a smart key from five to 20 meters and a vehicle equipped with Wi-Fi... well, it could be hacked from anywhere there's Internet access.
That may be a problem. Increasingly, carmakers are coming out with vehicles that include Wi-Fi routers for Internet connectivity, Gragg said.
"Of the 21,000 vehicles stolen in London in 2013, it is estimated 47% were subjected to some form of electronic hacking," the PT&C|LWG report states. "The majority of these hacks involved using electronic devices to fool the vehicle's security systems into believing a key was present."
Gragg said that "in the wild," the vehicles on the most-hackable list have yet to be compromised. The results of the study were based on attempts by engineers and white-hat hackers.
"In more advanced vehicles -- the ones that have infotainment systems -- wireless security and wireless access points are all connected into the navigation system. So those are more susceptible to hacking because there are just more wireless access points," Gragg said. "Anything open to wireless capabilities is susceptible to the hacking."


