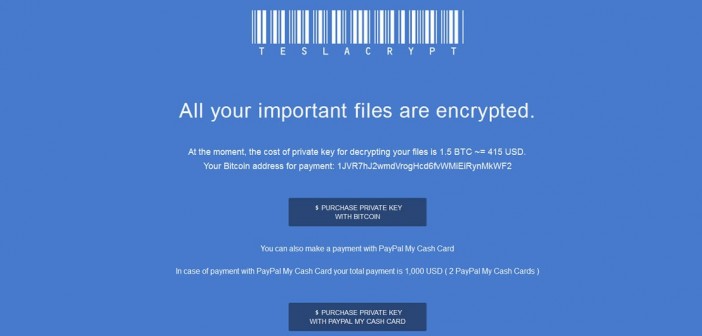
Experts at Bleeping Computer blog are reporting a new strain of ransomware dubbed LowLevel04 that is spreading via Remote Desktop and Terminal Service.
Security experts at Bleeping Computer blog are reporting a new strain of ransomware dubbed LowLevel04 that is using an unusual infection mechanism, it is being spread via Remote Desktop and Terminal Service. The LowLevel04 ransomware encrypts local files by using the AES encryption and demands a fee of 4 Bitcoin ($1,000 USD) as ransom to unlock them.
LowLevel04 was first spotted this month and a business owner on the Bleeping Computer support forum reported that his system has been infected by the ransomware. The malware included a ransom demand in the form of a text file (help recover files.txt) in each folder where a file was encrypted.
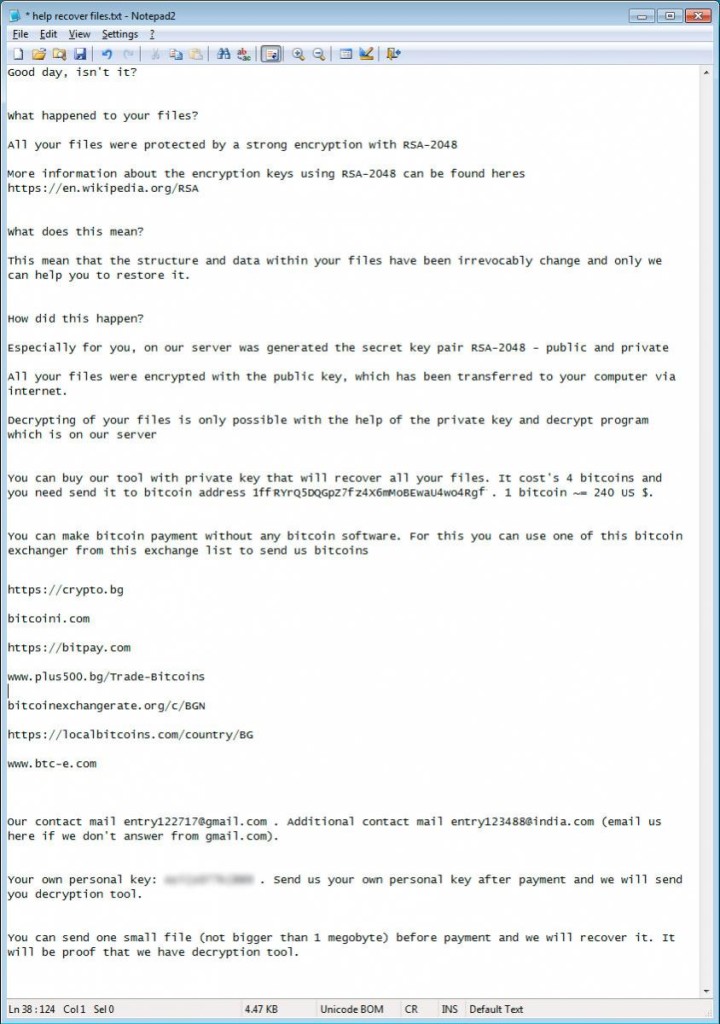
The file contains the instruction to get back the files and how to complete the payment of the ransomware, the bad actors are using the email addresses This email address is being protected from spambots. You need JavaScript enabled to view it. and This email address is being protected from spambots. You need JavaScript enabled to view it. to get in touch with victims.
The attackers run brute force attacks on targeted machines running Remote Desktop or Terminal Services.
Infections were observed in Greece and Bulgaria, the malware researcher Nathan Scott who analyzed the strain of LowLevel04 revealed that when it runs, it first scans all mapped drives, including removable ones, and network drives to encrypt files.
"When the ransomware executable is run it will scan all mapped drives, including removable and network drives, for data files to encrypt. When it encounters a file that contains certain file extensions it will encrypt them using AES encryption and then add the oorr. string to the beginning of the file name."
The format of the Encrypted Data File:
- Encrypted version of original file
- Original file size
- RSA encrypted encryption key
- Key size
- lowlevel04 string
"When a file is encrypted it will be recreated so that it contains different layers of information that can be used by the decrypter to decrypt your files. The different layers of the newly encrypted file are the encrypted contents of the original file, the original file size, the encrypted encryption key, the key size, and finally a lowlevel04 string that identifies that this is a file was encrypted by this particular infection. These layers of data in an encrypted file are shown below." states the blog post on the Bleeping Computer.
The expert noticed that the only way to recover files is via backup, restoring the Shadow Volume Copies that fortunately this ransomware does not delete. This means that victims can try a recovery by using the Shadow Explorer program.
For cloud services infected by LowLevel04, including Dropbox, victims are suggested to remove the oorr prefix from the encrypted files and revert back to a previous version.