TrapX, a renowned security providing delivery of deception based cybersecurity defense uncovered a security flaw in medical field dubbed as medical device hijack, or simply put MEDIJACk.
Let it be Anthem hack or CareFirst BlueCross BlueShield, this year has already experience a decent number of breaches within healthcare organizations. While various attacks and causes have been pointed out as the compromises by these providers, it never got stated as a prominent news that medical devices could be the true causes of breaches that took place and the ones that are going to be discovered sooner or later.
Trapx found that most of the medical organizations are vulnerable – if not a victim to MEDIJACK already, or simply put medical device hijack. The main networks of healthcare systems are initially exploited when hackers get to break into unpatched and outdated devices, like blood gas analyzer or X-ray scanner. The company wrote, the attackers build their backdoors into systems via such devices that are connected to the Internet.
General Manager at TrapX, Carl Wright wrote in an email to SCMagazine,
"Our scientists have observed that you could manufacture an attack, designed specifically for several models of a specific medical device, and then launch that attack". "That, combined with the difficulty in diagnosis and remediation, and the very high value of healthcare data, create a near perfect target for organized crime."
Various case studies have been conducted by TrapX where they found, most of the hospitals take good care of their IT departments with solid firewalls and other security solutions, while on the contrary – such devices are left without patching most of the times.
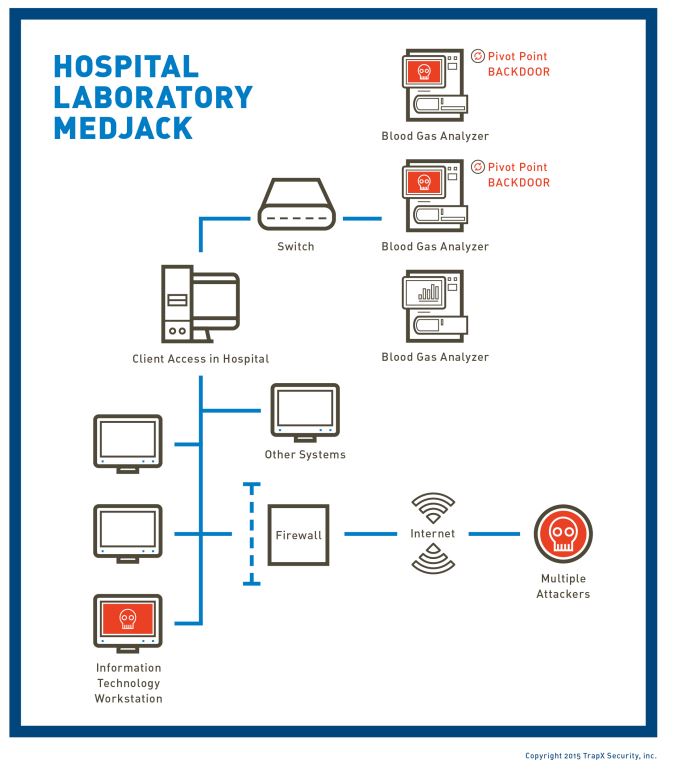 Typically, as the machines run for many days continuously, it never gets disconnected or even the security team remains unable to completely review the operating system console of the devices.
Typically, as the machines run for many days continuously, it never gets disconnected or even the security team remains unable to completely review the operating system console of the devices.
"Every malware infection that connects a network to an outside attack, in the United States, is a serious event and most likely would be categorized by that healthcare institution as a security event under their HIPAA operating procedures," Wright said. "Given that patient data is at risk, the medical device manufacturer needs to indicate exactly how they will respond to mitigate the situation so that a data breach can be contained or stopped, and normal hospital operations can resume."
All of the organizations who get aware of MEDIJACK threat, should devise a better security strategy, suggests Wright. Moreover, the professionals must ask device vendors how the devices support and invite them to aid in mitigating these attacks. The life cycle of each device should also be determined, and vendors should confirm if they make use of digitally signed software or not.
The software needs to be digitally signed, and life cycle will help a long way as the organizations will have a clear picture in mind as to when they should replace the old devices with new ones.
