Researchers from FireEye have revealed that it is possible to attack Android smartphone to remotely steal user's fingerprints on a "large scale."
Android device makers to release monthly security fixes
Google, Samsung and LG will start to issue monthly security patches for Android devices, taking a cue from the PC industry after critical vulnerabilities put hundreds of millions of smartphone users at risk.
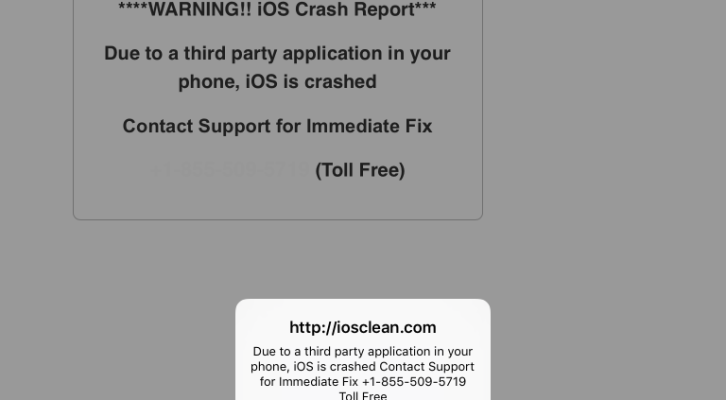
iOS crash warnings scam targeted iPhone and iPad users in US and UK
According to a report published by The Telegraph, scammers are targeting iPhone and iPad users with a new elaborate scheme that relies on iOS crash warnings Scammers are targeting iPhone and iPad users with a new-old elaborate scheme that relies on iOS crash warnings.
Android Users: This Simple Fix Will Help Keep You Safe From The Stagefright Exploit
Stagefright is a nasty potential problem for a huge majority of the World’s Android users. Thomas Fox-Brewster covered it in detail in his article yesterday, but here in brief is how to prevent the bug being used to access your phone without you even knowing.
Let's Make Mobile Security Easy
We often make things harder than they have to be by securing everything, when some things just aren’t as important as others. Often times, the steps we take to secure our mobile devices do not provide management or security benefits. They’re simply, “security theater,” or measures intended to provide the feeling of improved security while doing little or nothing to actually secure, like some of our favorite airport “security” practices.
Most Android phones can be hacked with a simple MMS message or multimedia file
The vast majority of Android phones can be hacked by sending them a specially crafted multimedia message (MMS), a security researcher has found.
Photo theft security loophole found in Android too
A security loophole on Apple's iOS platform that gives applications access to a user's photo library without explicit permission has been found to exist on Google's Android platform as well.