Security researchers have uncovered a group of fake recruiting accounts on LinkedIn used for intelligence gathering about security experts.
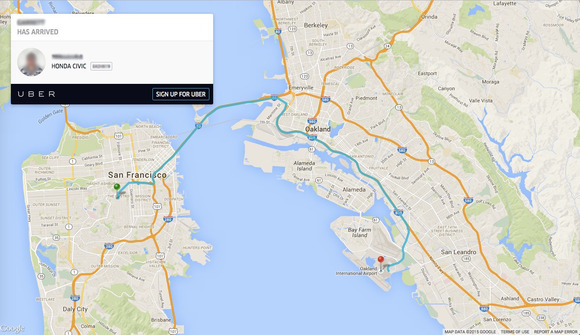
Some Uber ride data is publicly accessible through Google
Rapid diffusion of technology makes easy phenomena of accidental data leakage, the last one is related to the popular car service Uber. Dozens of trips of Uber customers have been cached by Google, making them available for searchers. Some Uber trip info is publicly accessible through Google by searching for "trip.uber.com" in Google.
BitTorrent patches flaw that could amplify distributed denial-of-service attacks
BitTorrent fixed a vulnerability that would have allowed attackers to hijack BitTorrent applications used by hundreds of millions of users in order to amplify distributed denial-of-service (DDoS) attacks.
he vulnerability was located in libuTP, a reference implementation of the Micro Transport Protocol (uTP) that's used by many popular BitTorrent clients including uTorrent, Vuze, Transmission and the BitTorrent mainline client.
Intel says GPU malware is no reason to panic, yet
Malware that runs inside GPUs (graphics processing units) can be harder to detect, but is not completely invisible to security products.
Researchers from Intel division McAfee Labs teamed up with members of Intel's Visual and Parallel Computing Group to analyze a proof-of-concept GPU malware program dubbed JellyFish that was released in March.
Project Unicorn offers $500,000 reward for Ashley Madison hackers
On Monday, Avid Life Media (ALM) announced a $500,000 CDN reward for information leading to the identification, arrest, and conviction of the person or persons responsible for the hack on Ashley Madison.
Tired of memorizing passwords? A Turing Award winner came up with this algorithmic trick
Passwords are a bane of life on the Internet, but one Turing Award winner has an algorithmic approach that he thinks can make them not only easier to manage but also more secure.
The average user has some 20 passwords today, and in general the easier they are to remember, the less secure they are. When passwords are used across multiple websites, they become even weaker.
Chinese spies target US intellectual property
It is not news that when it comes to economic espionage, China has been, in the words of a number of security executives, "eating our lunch" for decades.
But the more disastrous reality is that American companies, in large part due to grossly inadequate security measures, are essentially feeding their lunch to the Chinese (and other nations) – along with breakfast and dinner – experts in both the public and private sector say.