Researchers from the Massachusetts Institute of Technology (MIT) have discovered a vulnerability inTor which lead the identification of hidden services with up to 88 percent accuracy.
The team of experts composed of researchers from MIT and the Qatar Computing Research Institute (QCRI) will present their work at the next Usenix Security Symposium.
The discovery is disconcerting, the researcher demonstrated how to unmask Tor hidden services in the Tor Network by analyzing the traffic patterns of encrypted data passing through a single machine in the Tor network.
We have explained several times the routing algorithm implemented by the Tor network, “The Onion Router“, it allows to protect traffic by adopting several layers of encryption.
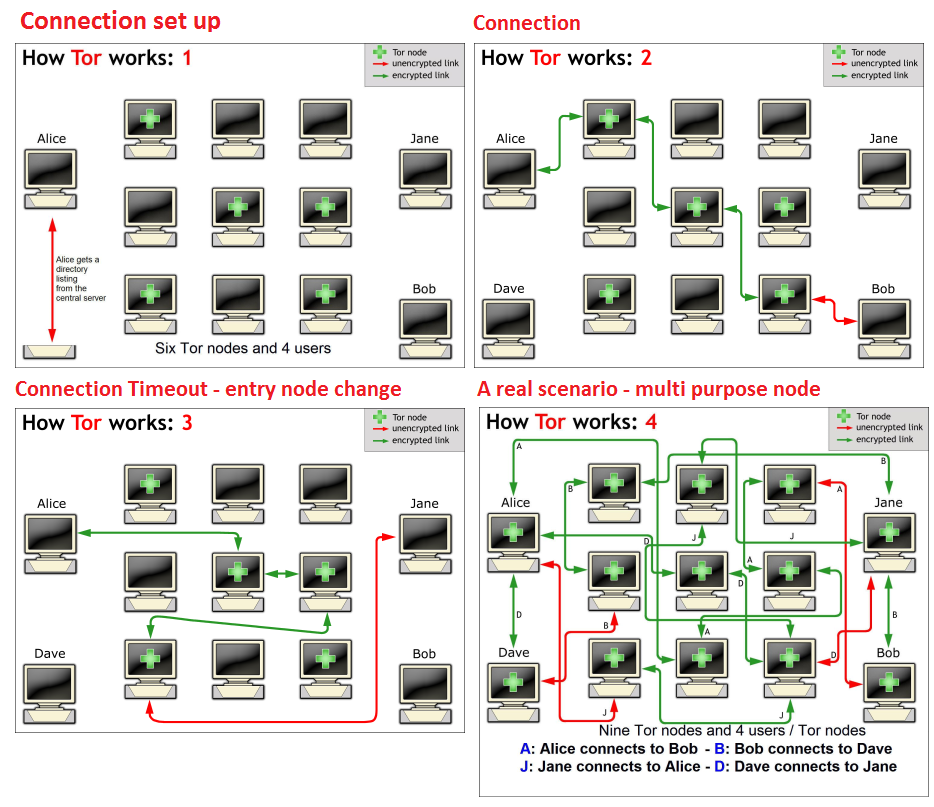
The routing process needs that machine in the Tor network exchange a large amount of data during the establishment of a connection to a hidden service.
The researchers demonstrated that “simply by looking for patterns in the number of packets passing in each direction through a guard, machine-learning algorithms could, with 99 per cent accuracy, determine whether the circuit was an ordinary Web-browsing circuit, an introduction-point circuit or a rendezvous-point circuit.”
The team run a traffic correlation attack, a hacking technique discussed several times when facing Tor hacking.
“Furthermore, by using a Tor-enabled computer to connect to a range of different hidden services, they showed that a similar analysis of traffic patterns could identify those services with 88 per cent accuracy. That means that an adversary who lucked into the position of guard for a computer hosting a hidden service, could, with 88 per cent certainty, identify it as the service’s host.” States the MIT’s full press release .
The experts also suggested a method to mitigate the attack by masking the sequences with dummy packers in a way they all look the same.
“We recommend that [the Tor project] mask the sequences so that all the sequences look the same,” said Mashael AlSabah, an assistant professor of computer science at Qatar University, as well as a researcher at QCRI and a visiting scientist at MIT. To defend against that kind of attack, he added, Tor needed to “send dummy packets to make all five types of circuits look similar.”
“For a while, we’ve been aware that circuit fingerprinting is a big issue for hidden services,” said David Goulet, a developer with the Tor project. “This paper showed that it’s possible to do it passively – but it still requires an attacker to have a foot in the network and to gather data for a certain period of time.”
“We are considering their countermeasures as a potential improvement to the hidden service,” he added. “But I think we need more concrete proof that it definitely fixes the issue.”
Which is the comment of the Tor Project?
A spokesman for the Tor Project confirmed to The Register that the attack presented by the boffins is a known issue, anyway it is difficult to carry on.
“It’s is a known issue that hidden service circuits are noticeable in certain situations, but this attack is very difficult to execute. The countermeasures described in the paper are interesting since the authors claim that deploying some of them would neutralize their attack and better defend against hidden service circuit fingerprinting attacks in general.” said the spokesman for the Tor Project. “We need more concrete proof that these measures actually fix the issue,” the spokesman continued, adding: “We encourage peer-reviewed research into both attacks against and defenses of the Tor network.”


