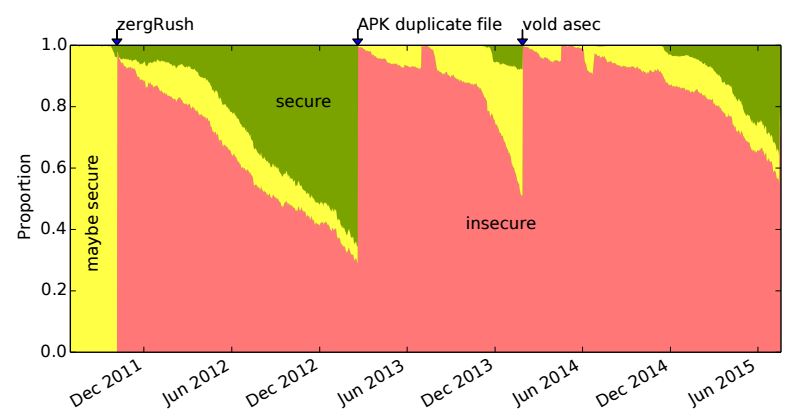
Researchers probed 20,400 Android devices and found 87.7 per cent contained at least one exploitable vulnerability due to a slow patch management.
New Android vulnerabilities are discovered every day, but it looks like that, some Android vendors are very slow in applying the necessary patch to fix the security issues. Some Android vendors are only fixing vulnerabilities once a year, this is the shocking revelation of a new study made by Daniel R Thomas, Alastair R Beresford, and Andrew Rice from the Cambridge University.
The trio proved 20400 devices and found out that 87.7% if the devices contain at least one big vulnerability, ready to be exploited.
In the Security Metrics for the Android Ecosystem paper, the experts explained the vulnerabilities (11) (i.e. dynamic link loading and injection) could let malware hijacking traffic, bricking mobile devices, replacing apps, and stealing user credentials.
"The security of Android depends on the timely delivery of updates to x critical vulnerabilities. Unfortunately few devices receive prompt updates, with an overall average of 1.26 updates per year, leaving devices un-patched for long periods. We showed that the bottleneck for the delivery of updates in the Android ecosystem rests with the manufacturers, who fail to provide updates to x critical vulnerabilities. This arises in part because the market for Android security today is like the market for lemons: there is information asymmetry between the manufacturer, who knows whether the device is currently secure and will receive updates, and the consumer, who does not. Consequently there is little incentive for manufacturers to provide updates." states the experts.
One good think that they proposed, is the creation metric that can be used by users and regulators to check the security risk related with the Android vendors. Below the metric used in the study:
The study also highlights that Nexus is the vendor that most of all constantly update its products.
Since the study was made in UK, they were only able to evaluate mobile carriers in that country, showing that O2 US is the best in pushing over-the-air security fixes, coming after T-mobile and Orange.
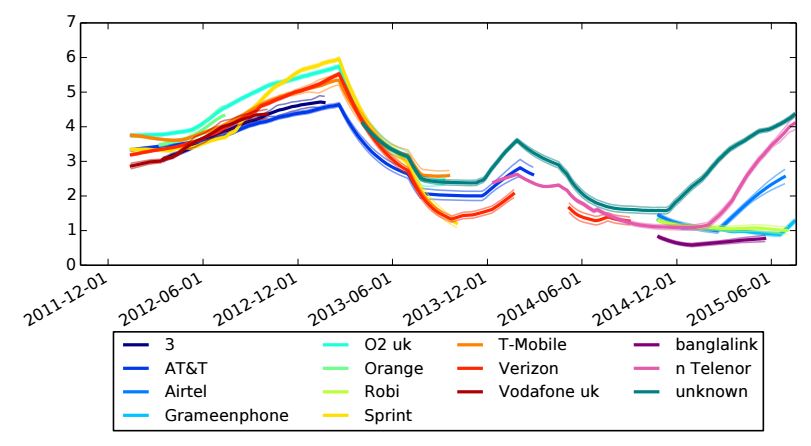
The patching architecture includes network operator, device manufactures, hardware developers, Google, and open source projects.
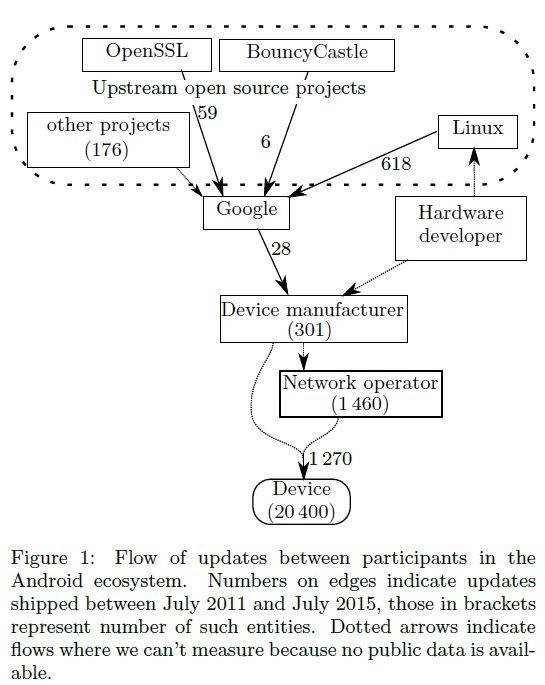 The criticality of the patch management is known for years, and it's not getting better, there are too many organizations in the middle before the patches arrive the end user, one solution could be that every patch is applied by Google to every device, and not being controlled by the mobile provider like it happens nowadays. In this way the entire patch management could be drastically improved providing more security for every Android owner.
The criticality of the patch management is known for years, and it's not getting better, there are too many organizations in the middle before the patches arrive the end user, one solution could be that every patch is applied by Google to every device, and not being controlled by the mobile provider like it happens nowadays. In this way the entire patch management could be drastically improved providing more security for every Android owner.